5 How vault items are secured
Items in your vaults are encrypted with Advanced Encryption Standard (AES) using 256-bit keys that are generated by the client on the device, using a cryptographically appropriate random number generator. This generated key becomes your vault key and is used to encrypt and decrypt the items in your vault.
1Password uses Galois Counter Mode (GCM) to provide authenticated encryption, protecting your encrypted data from tampering. Proper use of authenticated encryption offers a defense against a broad range of attacks, including Chosen Ciphertext Attacks (CCA).

Figure 5.1: Algorithm for creating and populating a vault
The vault key is used to encrypt each item in the vault. Items contain overviews and details that are encrypted separately by the vault key.8 We encrypt these separately so we can quickly decrypt the information needed to list, sort, and find items without having to decrypt everything in the vault first.
Item overviews include the item fields needed to list items and quickly match items to websites, such as Title, URLs, password strength indicator, and tags. Information that’s presented to the user when items are listed, along with the information needed to match an item to a web page (URL), are included in the overview.
Item details include the things that don’t need to be used to list or quickly identify them, such as passwords and contents of notes.
If you have access to a vault, a copy of the vault key is encrypted with your public key. Only you, the holder of your private key, are able to decrypt that copy of the vault key. Your private key is encrypted with key encryption key (KEK) derived from your account password and Secret Key.
Your private/public key pair is created on your device by your client when you first sign up. Neither we nor a team administrator ever have the opportunity to capture your private key. Your public key, being a public key, is widely shared.
5.1 Key derivation overview
Key derivation is the process that takes your account password and Secret Key and produces the keys you need to decrypt your data and to sign in to the 1Password server. It’s described more fully in “Key derivation.”
A cryptographic salt is a non-secret value that is added to either an encryption process or hashing to ensure that the result of the encryption is unique. Salts are typically random and unique.
Your account password will be trimmed and normalized. A non-secret salt is combined with your email address9 and other non-secret data using hash-based key derivation function (HKDF) to create a new 32-byte salt.
Your account password and the salt are passed to PBKDF2-HMAC-SHA256 with 650,000 iterations. This results in 32 bytes of data, which are combined with the result of processing your Secret Key.
Your Secret Key is combined with your non-secret account ID and the name of the derivation scheme by HKDF to produce 32 bytes of data. This will be XORed with the result of processing your account password.
The resulting 32 bytes of material (derived from both your account password and Secret Key) are your Account Unlock Key (AUK) which is used to encrypt the key (your private key) that’s used to decrypt the keys (vault keys) that are used to encrypt your data.
By encrypting copies of vault keys with an individual’s public key, it becomes easy to securely add an individual to a vault. This secure sharing of the vault key allows us to securely share items between users.
5.2 A first look at key sets
We organize the public/private key pairs together with the symmetric key that’s used to encrypt the private key into key sets. Our key sets make extensive use of JSON Web Key (JWK) objects.
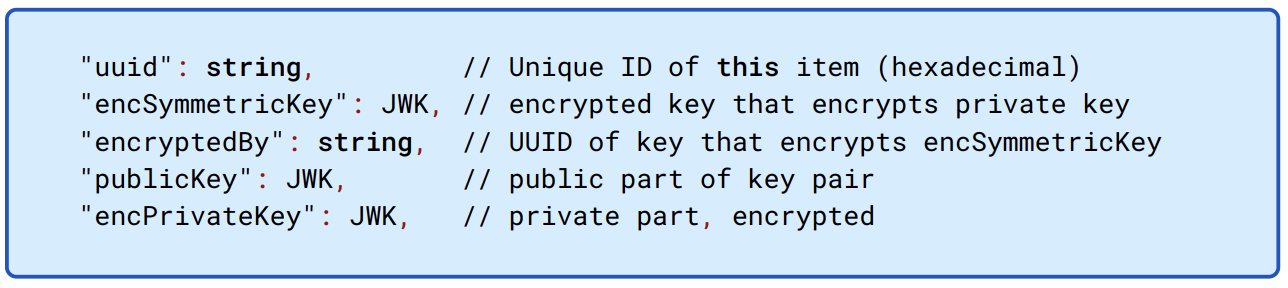
Figure 5.2: A key set is a collection of JWK keys together with an identifier and information about what other key set is used to encrypt it.
A common type of key set will have the structure listed in Figure 5.2. When we speak of encrypting a key set, we generally mean encrypting the symmetric key that’s used to encrypt the private key.
Key sets are fairly high-level abstractions; the actual keys within them have a finer structure that includes the specifications for the algorithms, such as initialization vectors. Symmetric encryption is AES-256-GCM, and public key encryption is RSA-OAEP with 2048-bit moduli and a public exponent of 65537.
In the beginning there was the vault, but it was empty and had no key.
And Alice’s 1Password client called out to the cryptographically secure random number generator, “Oh, give me 32 bytes,” and there were 32 random bytes. These 256 bits were called the “vault key.”
And the vault key was encrypted with Alice’s public key, so only she could use it; a copy of the vault key was encrypted with the public key of the Recovery Group, lest Alice become forgetful.
Alice went forth and named things to become part of her vault. She called forth the PIN from her account on the photocopier and added it to her vault. The photocopier PIN, both its details and its overview, were encrypted with the vault key.
And she added other items, each of its own kind, be they Logins, Notes, Software Licenses, or Credit Cards. And she added all of these to her vault, and they were all encrypted with her vault key. On the Seventh day, she signed out.
And when she signed in again, she used her account password, and 1Password used her Secret Key, and together they could decrypt her private key. With her private key she decrypted the vault key. And with that vault key she knew her items.
And Alice became more than the creators of 1Password, for she had knowledge of keys and items which the creators did not. And it was good.
Once a vault has been created, it can be securely shared by encrypting the vault key with the recipient’s public key.
5.2.1 Flexible, yet firm
Since the right choices for the finer details of the encryption schemes we use today may not be the right choices tomorrow, we need some flexibility in determining what to use. Therefore, embedded within the key sets are indications of the ciphers used. This would allow us to move from RSA with 2048-bit keys to 3072-bit keys, relatively easily when the time comes, or to switch to Ellipic Curve Cryptography (ECC) at some point.
Because we supply all the clients, we can manage upgrades without enormous difficulty.
Setting Some time in the not-so-distant future.
Day one “Hmm,” says Patty. “It looks like 2048-bit RSA keys will have to be phased out. Time we start transitioning to 3072-bit keys.”
The next day We ensure all our clients are able to use 3072-bit keys if presented with them.
Some weeks later We release clients that use 3072 bits when creating new public keys. (Public keys are created only when a new account is created or a new Group is created within a team.)
Further along ”We should go further and start replacing the older keys.” (Of course, we can’t replace anyone’s keys, as we don’t have them.)
After some development We issue updated clients that generate new public keys, and anything encrypted with the old key will be re-encrypted by the client with the new key.
Time to get tough We can have the server refuse to accept new data encrypted with the older keys. The server may not have the keys to decrypt these key sets, but it knows what encryption scheme was used.
More bad news on 2048-bit keys We learn that even decrypting stuff already encrypted with the older keys turns out to be dangerous. [Editor’s Note: This is a fictional story.] We need to prevent items encrypted with 2048-bit keys from being trusted automatically.
Drastic measures If necessary, we can issue clients that will refuse to trust anything encrypted with the older keys.
Building in the flexibility to add new cryptographic algorithms while limiting the scope of downgrade attacks isn’t easy. But as illustrated in Story 5, we’re the single entity responsible for issuing clients and managing the server, so we can defend against downgrade attacks through a combination of client and server policy.
The overviews and the details are encrypted with the same key. This is a change from the design of the OPVault 1Password data format described in OPVault Design (AgileBits 2015).↩︎
The reasons for binding your encryption key tightly with your email address are discussed in “Restoring a user’s access to a vault.”↩︎